Keep calm and sign your Software!
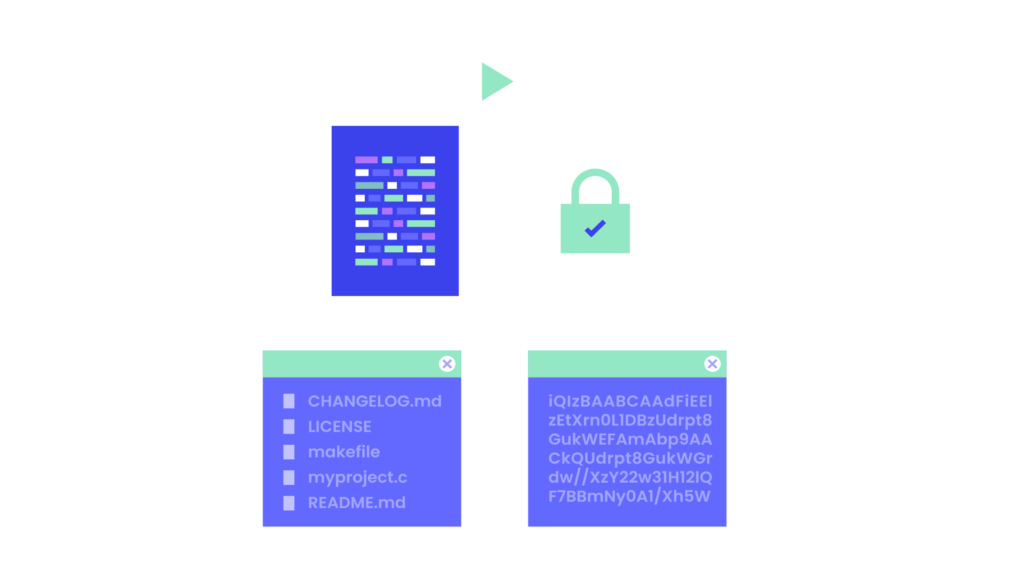
What is signed Software?
Digital signatures can be used to digitally sign software using public-key cryptography. A valid digital signature can be used to confirm the authenticity of the issuer and thus the integrity of the software. The most common software used to create digital signatures is GPG.
Why should you sign your Software?
Digitally signed software prevents attackers from manipulating your software on the way between you and the user. For example, by hacking the web space or manipulating the transport (download) of your software.

Who needs signed Software?
Digital signatures are not only important for security-conscious users, but especially for software packagers. The packaged software is distributed to a large number of users, therefore the security of the software is especially important.
How can I sign my Software?
To make it easy for you we have summarized the required steps into 5 simple steps.
We recommend that you work through the entire process once manually and then integrate it into your workflow using automated tools:

When is signed Software helpful and when is it not?
Signed software can significantly reduce the damage caused by infiltrating malicious software. Here you will find the most common attack scenarios, against which signed software does and does not help.
 Server/Mirror Hack
Server/Mirror Hack
The most obvious attack to spread manipulated software is to hack the software download server or its mirrors. Package maintainers who already know your GPG key will notice the manipulated software when checking its GPG signature.
 User Account Hack
User Account Hack
Even if you are already using a reasonably secure server (e.g. Github), it is still possible for an attacker to gain access to your user account. An attacker can then inject malicious code into your Git repository and create new software releases.
 Man-in-the-Middle-Attack
Man-in-the-Middle-Attack
A more complex and less likely way to inject tampered software is to manipulate the up- or download to/from the server. For example, a so-called man-in-the-middle intercepts an unsecured upload (ftp) or download (http). That’ s why it is so important to use additional secure protocols (https, ssh, etc.) for up- and downloading software.
 Leaking the private GPG Key
Leaking the private GPG Key
It is very important to keep your GPG key private. Make sure to use a strong passphrase and never publish it on untrusted devices or external servers. If the initial GPG key exchange is intercepted (by one of the threats above), the user likewise has no chance to verify the software authenticity.
 Security Issues within the Software itself
Security Issues within the Software itself
Of course, digital signatures do not protect against vulnerabilities in the software itself (or its dependencies). Make sure you trust the publisher of the software and review any code changes e.g. through an independent security audit.

Frequently Asked Questions
 Which popular Projects already use digital Signatures?
Which popular Projects already use digital Signatures?
 Which Projects have been compromised in the past?
Which Projects have been compromised in the past?
- Perl.com Domain Hijacking (2021)
- Canonical Github Account hacked (2019)
- Gentoo Github Account hacked (2018)
- Handbrake server compromised (2017)
- Linux Mint hacked ISOs (2016)
Do you know of any other examples? Let us know!
 Aren’t Github Projects already sufficiently secured?
Aren’t Github Projects already sufficiently secured?
Yes and no. It may be less likely that Github servers will be successfully attacked, but it is definitely not impossible that individual Github accounts will be hijacked. The above listing shows very clearly that this can happen even to very reputable projects, so you’d better not rely on it.
 Does it matter for my (small) Project?
Does it matter for my (small) Project?
As soon as your software is used by other users, it makes sense to secure it accordingly. It doesn’t matter if the software is a complex GUI program, a simple script, theme or anything else. Even supposedly “unimportant” projects can cause serious damage to users if malicious files with system privileges are installed.
 Are Hashes (SHA256, SHA1, MD5) sufficient?
Are Hashes (SHA256, SHA1, MD5) sufficient?
No. Hashes only ensure the integrity of the software, but never its authenticity.
 Can I use my GPG Key for E-Mail Encryption as well?
Can I use my GPG Key for E-Mail Encryption as well?
Yes. Especially if you have been planning to set up email encryption for a long time, now is the right time. By setting up a GPG key, you can sign your software and encrypt your emails from now on.